Ships face serious risks without secure voice communication. Outdated systems leave vessels vulnerable to eavesdropping, spoofing, and failures, which can result in safety hazards, disrupted operations, and even national security threats. Modern secure voice solutions solve these problems by encrypting conversations, ensuring only authorized personnel can access critical communications, and maintaining reliability even in emergencies.
Here’s why secure voice communication is essential for maritime operations:
- Prevents Eavesdropping: Encryption protects sensitive information like routes, cargo data, and safety instructions from being intercepted by malicious actors.
- Thwarts Spoofing: Authentication ensures only verified parties can send or receive instructions, reducing risks of false commands or misdirection.
- Improves Reliability: Redundant systems and failover mechanisms keep communication lines open during hardware or network failures.
- Streamlines Operations: Unified platforms integrate radios, intercoms, and satellite links, simplifying coordination between crew, ports, and shore teams.
- Ensures Compliance: Modern systems meet cybersecurity and safety standards, helping operators avoid regulatory penalties.
For U.S. waters and defense missions, these systems are especially critical to safeguard patrol routes, logistics, and mission plans. Companies like NT Maritime provide encrypted, reliable solutions tailored to various vessel types, ensuring safe and efficient communication at sea. Investing in secure voice communication is a smart move to protect your crew, cargo, and operations.
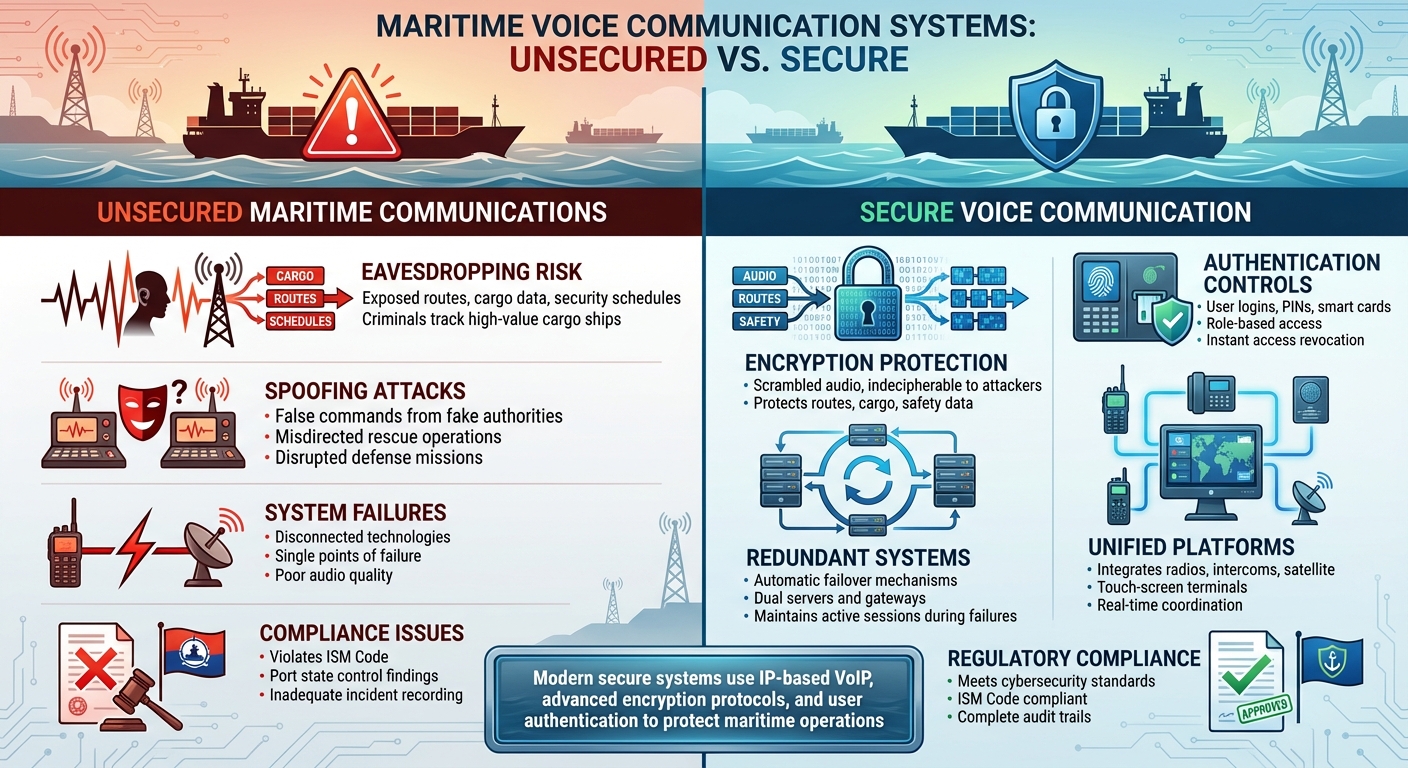
Risks of Unsecured vs Benefits of Secure Maritime Voice Communication
What Is Secure Voice Communication in Maritime Operations?
Defining Secure Voice Communication
Secure voice communication in maritime operations involves protecting voice calls through encryption, authentication, and a resilient network setup. This ensures conversations remain private and protected from interception, tampering, or disruptions while at sea. Unlike older shipboard systems that rely on analog radios or outdated PBX setups without strong encryption, modern secure systems use IP-based VoIP technology, advanced encryption protocols, and user authentication to restrict access to authorized personnel only.
These systems are built on a fast and reliable network framework that integrates both voice and data channels, eliminating single points of failure. For example, redundant VoIP gateways automatically take over in the event of a failure, allowing active sessions to continue without interruption. This design is particularly crucial for vessels operating in remote areas, where equipment breakdowns could compromise safety. Such a setup supports a wide range of communication needs, both within the ship and with external entities.
Common Uses of Secure Voice Communication
Secure voice systems serve a variety of critical functions, both onboard and in external communications. Internally, they facilitate intercom communication between key areas like the bridge, engine room, cargo hold, security posts, and medical centers. These systems allow crews to coordinate navigation, engineering tasks, and safety operations during maneuvers, cargo handling, or emergency drills, with access limited to authorized participants. Integration with emergency and public address systems ensures that urgent messages are delivered instantly and securely to all relevant zones, originating only from verified sources.
Externally, secure voice communication connects ships with ports and harbor authorities for tasks like pilotage, tug coordination, and berthing instructions, often using VHF radio and integrated telephony. It also enables communication between vessels for collision avoidance or search-and-rescue efforts, with aircraft during inspections or transfers, and with shore-based operations centers via SATCOM and long-range radio. These channels often carry sensitive commercial data – such as routes, cargo details, and schedules – as well as critical safety information like distress signals and hazard alerts. Encryption and authentication ensure that only legitimate parties can access these communications and that instructions remain intact, preventing interference from potential adversaries.
NT Maritime‘s Secure Voice Solutions
NT Maritime offers advanced secure communication solutions for commercial, cruise, and government or military vessels. Their systems provide encrypted onboard calling, messaging, video calls, and voicemail over ship WiFi. Specifically designed for federal and military use, these systems are built to withstand cyber threats while meeting strict compliance standards required for mission-critical operations.
The platform supports a variety of call types, including App-to-App calls, App-to-Ship PBX calls, Ship PBX-to-App calls, and App-to-Off-Ship calls. This flexibility allows crew members and passengers to coordinate internally and communicate seamlessly with shore-based teams. For cruise ships, NT Maritime also integrates features like Hotel-to-Guest and Guest-to-Guest calling, ensuring that operational and safety channels remain secure and isolated from guest communication systems. By uniting voice, data, and messaging on a single, secure network, NT Maritime helps vessels maintain clear and protected communication across all operations, both onboard and external. These capabilities address the vulnerabilities and risks mentioned earlier, highlighting the importance of modern, secure communication systems in ensuring maritime safety.
Leonardo DRS SHINCOM Shipboard Integrated Communications
Risks of Unsecured Maritime Communications
Understanding how secure systems work is just one side of the coin. It’s equally important to grasp the dangers posed by unsecured maritime communications.
Cybersecurity Threats: Interception and Spoofing
When maritime communications aren’t encrypted, they become an open book for anyone to intercept. This can expose critical details like vessel positions, route changes, security schedules, cargo information (measured in U.S. dollars), and even technical vulnerabilities that might be casually discussed over open channels.
Attackers can take advantage of this by spoofing trusted sources – think port authorities or the coast guard. This tactic can mislead crews into making course adjustments, misdirect rescue operations, or even disrupt defense missions. For instance, during U.S. government or military operations, spoofed instructions could delay responses, scatter formations, or push a vessel into a strategically weaker position.
There are documented cases where criminals have exploited open marine radio traffic to track high-value cargo ships or tankers, time their attacks, or target less-defended vessels. Security drills have also shown how false radio transmissions on coastal channels can create chaos – triggering false alarms, misdirecting patrols, and throwing off critical operations in U.S. ports.
Inefficiencies from Outdated Systems
Many maritime communication systems rely on outdated, disconnected technologies for radio, intercom, telephone, and PA systems. This lack of integration slows down the flow of information and increases the chances of miscommunication – especially during emergencies. Without a unified communication platform, it’s difficult to coordinate between the bridge, engine room, cargo hold, and shore, or to monitor multiple channels from a single interface.
Older analog systems and a mishmash of legacy equipment often come with poor audio quality, inconsistent user interfaces, and limited functionality. Crew members are left to memorize complex procedures and channel plans for different devices. In high-pressure situations, like emergencies or heavy traffic, this can lead to dialing the wrong party, missing critical calls, or misinterpreting instructions due to static or poor sound clarity.
Safety and Regulatory Compliance Issues
Emergencies – whether it’s a fire, flooding, collision, or medical crisis – demand reliable communication. But non-redundant systems can fail when they’re needed most, cutting off essential coordination and putting lives at risk. Without backup IP networks, a single hardware failure or broken link can sever both radio and internal voice communications.
Regulators and industry standards are increasingly emphasizing the importance of secure and dependable communication systems as part of broader safety and cybersecurity protocols. Using unencrypted links to handle sensitive operational information can violate evolving maritime cybersecurity guidelines and the International Safety Management (ISM) Code. This could lead to negative findings during audits or inspections by port state control. Furthermore, inadequate recording capabilities, lack of system redundancy, and frequent outages can complicate incident reporting and evidence collection after accidents or security breaches.
These vulnerabilities underscore the pressing need for secure, modern communication systems to ensure safer, more efficient maritime operations.
sbb-itb-bda822c
How Secure Voice Communication Solves Maritime Problems
Now that we’ve explored the risks, let’s shift focus to how secure voice communication tackles these challenges head-on with encryption, unified platforms, and emergency-ready systems.
Enhanced Security with Encryption and Authentication
Encryption ensures voice traffic remains private, scrambling audio so only devices with the right keys can decode it. Modern encryption methods render intercepted data useless, whether it’s RF, satellite, or IP traffic. For attackers, this means capturing nothing but indecipherable noise, which greatly reduces the chances of espionage or data breaches.
Authentication tools like user logins, PINs, smart cards, and role-based access controls add another layer of security. Centralized management consoles oversee access, allowing administrators to track login attempts, configure user roles, and instantly revoke access if a device is lost or a crew member rotates out. This proactive approach plugs potential security gaps in daily operations.
Smoother Operations with Unified Communication Platforms
Security isn’t the only benefit – unifying communication channels boosts operational efficiency. Modern maritime communication platforms bring together analog and IP radios, telephones, intercoms, and satellite links into one manageable system. Crews can access all these channels through intuitive touch-screen terminals, simplifying tasks like switching between VHF/UHF radios, internal intercoms, or external phone calls.
Server-based VoIP gateways bridge the gap between analog radios, older telephony systems, and modern IP voice services. This seamless integration allows crew members, pilots, harbor authorities, and shore operations to connect without the hassle of manual patching. For complex operations like docking, cargo handling, or launching smaller vessels, this unified approach ensures the engine room, deck, and bridge stay in sync with real-time, clear communication.
By unifying systems, these platforms also create a solid foundation for emergency communications.
Reliable Support During Emergencies
In critical situations, integrated systems prioritize distress calls and automatically switch to backup servers to ensure communication remains uninterrupted, even in extreme conditions. With a single console, the bridge can coordinate with all key teams, minimizing confusion. Emergency protocols – like prioritizing mayday or distress calls – ensure vital messages cut through and avoid congestion, even when bandwidth is stretched thin.
Redundant networks add another layer of reliability, keeping communication lines open during system failures. Ruggedized terminals and loudspeakers are built to withstand intense conditions like high noise, vibration, salt spray, and humidity. These systems deliver clear audio, whether on deck, in the engine room, or in exposed areas. For demanding tasks like boarding operations or coordinating between the main ship and smaller vessels (RHIBs) in noisy, high-salinity environments, tactical headsets and loudspeakers ensure real-time command and control remains intact.
Steps to Implement Secure Voice Communication on Ships
Evaluating Current Communication Infrastructure
Start by taking stock of all the voice communication devices on board, such as bridge phones, intercoms, radios, PA/GA systems, satellite phones, and softphones. Document each device’s specifications and software versions. Then, map out all communication pathways – whether they’re ship-to-ship, ship-to-shore, ship-to-air, or internal channels. Determine which systems use IP protocols, which are analog, which operate on radio frequencies, and whether any form of encryption is already in place.
Look for system redundancies to identify potential single points of failure, such as servers, gateways, or power supplies. Check if there are redundant pathways or automatic failover mechanisms. Additionally, review access controls for consoles, network segmentation, and compliance with regulatory voice recording requirements.
If your systems already support IP-based protocols like SIP, can connect to VoIP gateways, and are compatible with external encryption devices, they are ready for secure integration. However, if you’re dealing with outdated analog hardware that lacks vendor support, has no encryption, or experiences frequent outages affecting safety operations, a complete replacement may be necessary.
This thorough evaluation lays the groundwork for designing a secure and reliable communication system.
Designing and Deploying Secure Solutions
When designing secure communication systems, focus on four key principles: encryption, redundancy, interoperability, and survivability. These address both cybersecurity concerns and operational challenges. Start by encrypting all voice traffic across the ship’s LAN, satellite connections, and shore links. Build redundancy into the system with dual communication servers, backup VoIP gateways, and mirrored databases to ensure active sessions are preserved during hardware or connection failures.
Use open-standard protocols like SIP-based VoIP, which integrate smoothly with existing radio and satellite systems while maintaining secure communication channels. For hardware, select ruggedized terminals that meet Defense Standards (DEF-STAN) or MIL-STD specifications, ensuring durability against harsh conditions like vibration, salt spray, and electromagnetic interference – especially in exposed or high-risk areas like the engine room.
Roll out the system in phases, starting with pilot tests and staggered deployments during maintenance windows. Keep legacy systems operational as temporary backups during the transition. Centralized configuration tools can simplify the process, allowing call flows, user roles, and encryption policies to be quickly duplicated across multiple ships.
Crew training is essential. Provide role-specific training for bridge teams, engineers, security personnel, and medical staff. Conduct drills that simulate real-world scenarios, such as server outages, switching to backup channels, initiating group calls, or using secure communication during emergencies like fires or collisions. Simplified touch-screen interfaces and unified consoles can reduce training time from weeks to just a few days, which is particularly important for rotating crews. Secure voice procedures should also be integrated into the ship’s Safety Management System to ensure they are regularly audited and updated.
How NT Maritime Supports Implementation
Once a secure system design is finalized, the next step is smooth implementation, and this is where NT Maritime excels. Their approach ensures both system integrity and operational continuity.
NT Maritime begins by assessing existing onboard networks and communication hardware. They identify opportunities to integrate secure voice services alongside Telehealth and crew or passenger communication tools, all while maintaining logical separation on a high-speed backbone. Their designs combine onboard calling, messaging, video calls, and voicemail with secure voice capabilities tailored to the needs of cruise lines, commercial fleets, and government or military vessels.
During deployment, NT Maritime provides preconfigured equipment and manages the project to align with vessel schedules. They also offer structured crew training and detailed documentation to ensure a smooth transition. Post-deployment, NT Maritime delivers round-the-clock support, monitoring, and regular security reviews to keep encryption standards, firmware, and configurations up to date. Operators can confidently expand services, such as adding new Telehealth features or crew tools, without compromising the security or reliability of the core voice communication system.
Conclusion
Secure voice communication plays a critical role in ensuring safety, efficiency, and compliance in maritime operations. Outdated systems leave vessels vulnerable to interception, spoofing, and system failures. In contrast, modern IP-based, encrypted voice platforms address these risks while seamlessly connecting bridge, engine room, and shore communications. These platforms are designed to remain operational even during hardware or connection failures, offering a reliable solution for today’s maritime challenges.
For U.S. operators managing vessels worth millions, the cost of implementing secure voice infrastructure is a fraction of the potential losses from collisions, cargo damage, or cyberattacks. Encrypted communication systems not only enhance security but also streamline workflows, reducing delays and errors while improving fleet oversight. During emergencies like distress calls, man-overboard situations, or fires, secure voice systems provide dependable, clear coordination – often the deciding factor between successful outcomes and operational setbacks. This level of reliability builds trust in secure communication systems when they are needed most.
"Secure communications for federal and military deployments ensure encrypted, reliable, and real-time information exchange. Built to withstand cyber threats, we support mission-critical operations with robust protection and compliance." – NT Maritime
To safeguard your operations, start by assessing communication risks and defining your needs based on vessel type and regulatory requirements. Collaborate with maritime communication experts like NT Maritime to develop a secure, unified system. Your plan should include encryption, redundancy, long-term voice recording, and compatibility with existing radios and IT networks. By investing in secure voice communication, you prepare your fleet for current challenges and future advancements, such as enhanced monitoring and telehealth services, ensuring the safety of your crew, cargo, and reputation.
Vessels equipped with secure, unified communication systems can navigate today’s complex maritime environment with confidence, meeting regulatory requirements while laying the groundwork for the next generation of digital operations.
FAQs
How does secure voice communication protect shipboard conversations from being intercepted?
Secure voice communication ensures that conversations on ships remain private by encrypting voice data, making it unintelligible to anyone without proper authorization. Additionally, it incorporates strong authentication protocols to confirm that only approved personnel can access the communication channels. This dual-layer of protection helps keep sensitive information confidential and strengthens overall operational security onboard.
What makes NT Maritime’s secure voice solutions essential for maritime operations?
NT Maritime offers secure voice solutions tailored to the demanding environment of maritime operations. With encrypted communication, these services enable passengers and crew to stay connected through onboard calling, messaging, and video calls, ensuring smooth and secure interactions even while at sea.
By protecting sensitive information from potential breaches and enhancing operational workflows, these solutions play an essential role in both commercial and government or military maritime missions.
Why is it important to modernize maritime communication systems?
Modernizing communication systems in the maritime industry is crucial for protecting sensitive information, boosting efficiency, and maintaining reliable connectivity for essential services like emergency response and Telehealth. Relying on outdated systems increases the risk of data breaches and communication breakdowns, which can jeopardize both safety and productivity on board.
By upgrading to modern solutions, vessels gain access to secure and dependable voice communication, along with advanced tools designed specifically for maritime operations. These improvements not only streamline day-to-day activities but also enhance safety measures for both the crew and passengers.