Cybersecurity risks in the maritime industry are growing as ships increasingly depend on interconnected IT and OT systems for navigation, propulsion, communication, and cargo handling. These systems improve efficiency but also expose vessels to potential cyberattacks, which can disrupt operations, compromise safety, and lead to financial losses or regulatory penalties.
Key points covered in this guide:
- Rising Cyber Threats: Ships face risks like ransomware, GPS spoofing, phishing, and outdated systems.
- Regulations: Compliance with IMO Resolution MSC.428(98) and U.S. Coast Guard standards is mandatory.
- Risk Assessment Steps: Define scope, inventory assets, identify vulnerabilities, analyze risks, and plan mitigations.
- Mitigation Strategies: Use tools like network segmentation, secure remote access, multi-factor authentication, and crew training.
- Governance and Compliance: Maintain a cyber risk register, conduct regular audits, and ensure fleet-wide consistency.
This guide provides practical steps to identify, prioritize, and reduce cyber risks, ensuring safer and more compliant maritime operations.
Understanding Maritime Cyber Risks
Ship IT and OT Systems Overview
Modern ships rely on two key types of systems: Information Technology (IT) and Operational Technology (OT). IT systems manage data processing, communication, and administrative tasks, while OT systems control and monitor physical processes. These processes include navigation tools like ECDIS, GPS, AIS, and radar, as well as propulsion, steering, power management, cargo handling, and safety equipment .
The challenge arises from the increasing interconnection between these systems. For instance, route planning done on office IT networks can directly feed into navigation displays on the ship’s bridge. Similarly, shore-based teams might monitor machinery performance remotely. According to the International Maritime Cyber Security Organisation (IMCSO), ten critical OT infrastructure categories – including navigation, propulsion, and safety systems – require thorough evaluation. When IT and OT networks share infrastructure or data paths, vulnerabilities in one can cascade into the other. For example, malware originating on an administrative laptop could infiltrate safety-critical systems if proper network segmentation isn’t in place .
Modern ships also connect to external networks through satellite communications, terrestrial links in port, USB drives, remote diagnostic connections, and even crew Wi-Fi. Each of these access points introduces potential risks if not properly secured . The complexity of these systems is compounded by the fact that ships often have dozens of interconnected control systems that must operate smoothly while staying secure. While IT-OT integration improves functionality, it also creates multiple avenues for cyberattacks.
Common Cyber Threats to Ships
Maritime vessels face a range of cyber threats that can disrupt operations or jeopardize safety. One of the most alarming is ransomware, where attackers encrypt critical systems and demand payment to restore them. This could disable essential systems like navigation or propulsion, forcing vessels to halt operations .
GPS spoofing and jamming are particularly dangerous at sea. Attackers can broadcast false GPS signals, leading ships to miscalculate their position and potentially stray into restricted or hazardous waters. Similarly, manipulation of AIS data can create confusion about vessel locations and movements, complicating collision avoidance . Phishing attacks, often targeting crew members and shore staff, aim to steal credentials and gain access to sensitive systems.
Other threats include malware introduced via USB drives or email attachments, denial-of-service attacks that overwhelm shipboard or shore systems, and unauthorized remote access to OT systems. Many vessels still rely on outdated IT and OT systems, which often run on older operating systems that are difficult to patch. Weak access controls, default passwords, poor network segmentation, and limited logging capabilities further exacerbate these vulnerabilities .
The consequences of these vulnerabilities are severe. Cyber incidents can lead to navigation failures, propulsion or steering issues, cargo and ballast system malfunctions, disrupted port schedules, safety system failures, financial losses, environmental harm, and damage to a company’s reputation . Additionally, the involvement of multiple stakeholders – such as shipowners, operators, charterers, port authorities, and vendors – can create accountability gaps, making it unclear who is responsible for cybersecurity.
Regulatory and Compliance Requirements
Given the risks, robust compliance frameworks are critical. The International Maritime Organization (IMO) established Resolution MSC.428(98), which mandates that cyber risks be addressed as part of Safety Management Systems (SMS). Compliance with this requirement has been mandatory since January 1, 2021 .
In the U.S., the Maritime Transportation Security Act (MTSA) of 2002 requires maritime facilities to conduct Facility Security Assessments that include identifying cybersecurity vulnerabilities . The U.S. Coast Guard’s Maritime Cybersecurity Assessment and Annex Guide (MCAAG) provides a structured approach to identifying and mitigating cybersecurity risks, integrating cyber considerations into physical security planning.
Industry organizations like BIMCO, ICS, CLIA, INTERTANKO, and INTERCARGO have developed "Guidelines on Cyber Security Onboard Ships" to help meet IMO requirements. These guidelines cover areas such as risk assessment, network architecture, access control, incident response, and crew training. Additionally, classification societies like DNV and ABS offer their own methodologies for cyber risk management. The IMCSO has recently introduced a standardized cybersecurity assessment methodology that helps stakeholders like insurers and port authorities create consistent risk profiles across vessels.
These frameworks provide vessel operators with tools to navigate a complex compliance environment, where flag states, port authorities, charterers, and insurers may impose additional requirements beyond IMO standards.
Update on maritime cybersecurity threats and mitigation methods
How to Conduct a Cyber Risk Assessment
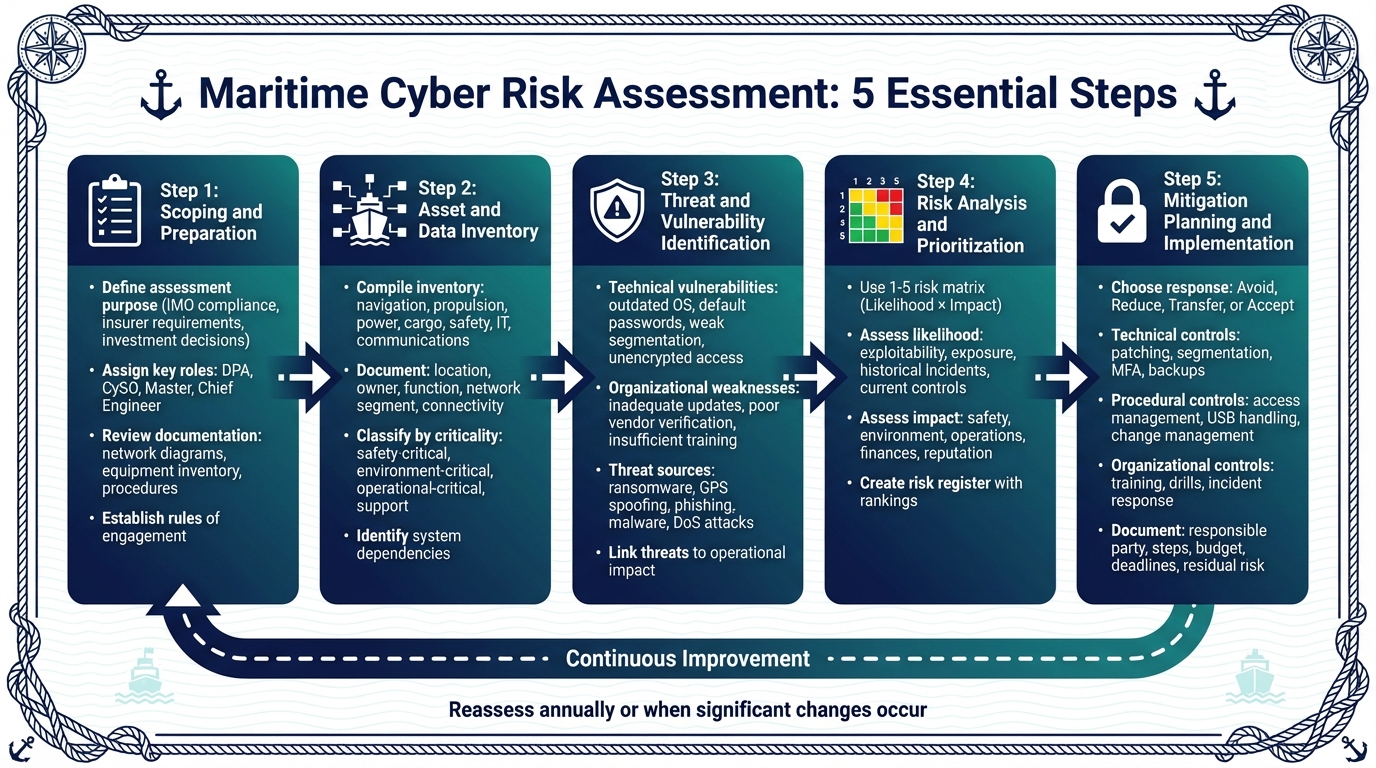
5-Step Maritime Cyber Risk Assessment Process
Scoping and Preparation
Start by defining the purpose of your assessment. Are you aiming to meet IMO standards, satisfy insurer requirements, or guide investment decisions? Clarify which vessels, operational phases (like at sea, in port, or in dry dock), and domains (such as navigation, propulsion, cargo handling, passenger services, crew communications, and shore links) will be included in your scope .
Next, assign responsibilities to key personnel. This might include the Designated Person Ashore (DPA), Cybersecurity Officer (CySO), ship’s master, chief engineer, and IT/OT vendors. According to the U.S. Coast Guard’s Maritime Cybersecurity Assessment and Annex Guide (MCAAG), the CySO plays a central role in coordinating the assessment .
Review all relevant documentation – network diagrams, equipment inventories, safety management procedures, class and flag requirements, and past incident reports or audits . Establish clear rules of engagement for the assessment. These should detail what can be tested, testing schedules, data handling protocols, and reporting formats, ensuring minimal operational impact. Following these steps not only makes the process repeatable across a fleet but also helps reduce disruptions . Once prepared, document your assets to create a comprehensive map of your cyber environment.
Asset and Data Inventory
Compile a detailed inventory of all onboard systems, including navigation, propulsion, power, cargo, safety, IT, and crew and passenger communication systems . For each system, note its location, owner, function, network segment, connectivity (including remote access), data it processes, and any backup or redundancy features .
Classify these assets by their criticality – whether they are safety-critical, environment-critical, operational-critical, or support-related. Identify dependencies, such as how an ECDIS (Electronic Chart Display and Information System) relies on GPS and accurate time sources. If passenger and crew communications share infrastructure with operational systems, detail how they are segregated. This could range from strict firewall rules to logical VLANs with varying levels of access control .
Keep this inventory updated as a controlled document, with versioning and periodic reviews as required by maritime cyber guidelines . For example, the CRASH methodology has demonstrated scalability by assessing 24 distinct cyber risks for an Integrated Navigation System with 25 components. With a well-maintained inventory, you can move on to identifying vulnerabilities.
Threat and Vulnerability Identification
Leverage a variety of resources to identify potential threats. These can include historical maritime incidents, vendor advisories, vulnerability databases, and frameworks like MITRE ATT&CK . Look for technical vulnerabilities such as outdated operating systems, default passwords, weak network segmentation, unencrypted remote access, missing patches, shared accounts, and improper USB use on bridge systems .
Don’t overlook organizational and procedural weaknesses, like inadequate update protocols, poor vendor access verification, insufficient crew training, or weak personnel management practices . Tie each identified threat to its potential operational impact, such as loss of propulsion, voyage delays, cargo damage, or service interruptions .
Risk Analysis and Prioritization
Use a 1–5 risk matrix to evaluate and rank risks by their likelihood and impact . Likelihood can be assessed by examining factors like the exploitability of vulnerabilities, exposure to external networks, historical incidents in similar fleets, and the effectiveness of current controls (e.g., patch management, system hardening, and crew training) .
Assess the impact of each risk on safety, the environment, operations, finances, and reputation. Predefined criteria, such as "loss of propulsion", "voyage delays exceeding 24 hours", or "regulatory non-compliance", can help guide this process. Record and rank each risk in a risk register, ensuring that each entry is linked to the relevant assets, threats, and vulnerabilities, along with a clear rationale for its score .
Mitigation Planning and Implementation
Based on the risks identified, create a mitigation plan that aligns with compliance requirements. For each high or medium risk, determine an appropriate course of action: avoid (change processes to eliminate the risk), reduce (implement controls), transfer (e.g., through insurance or contracts), or accept (with documented justification) .
Choose controls that align with maritime cyber best practices. These may include technical measures like patching, network segmentation, multi-factor authentication, secure remote access, and backups; procedural measures like access management, USB/media handling, and change management; and organizational measures like training, drills, and incident response plans .
When planning mitigations, consider the unique constraints of ship operations, such as limited bandwidth, restrictions on modifying OT systems, and crew workload . For each mitigation, document the responsible party, required steps, budget, deadlines, and the residual risk rating .
For communication-related risks – such as segregating passenger and crew services, securing remote access, or managing telehealth traffic – solutions like those offered by NT Maritime can be invaluable. Their services include secure communication networks, traffic segregation, encryption, and access controls, which address vulnerabilities in these areas . Documenting these measures as part of your corrective action plan not only demonstrates risk reduction but also strengthens your vessel’s overall security posture while meeting maritime cybersecurity standards.
sbb-itb-bda822c
Tools and Best Practices for Risk Mitigation
Reference Frameworks for Maritime Cybersecurity
To establish a strong cybersecurity foundation, ship operators should align their programs with recognized frameworks that address both IT and operational technology (OT). The International Maritime Organization (IMO) Guidelines on Maritime Cyber Risk Management (MSC-FAL.1/Circ.3) offer high-level guidance structured around key functions: identify, protect, detect, respond, and recover. Additionally, Resolution MSC.428(98) mandates integrating this guidance into Safety Management Systems under the ISM Code.
The NIST Cybersecurity Framework (CSF) provides a clear structure for organizing existing policies into a cohesive cybersecurity program, which is also applicable in maritime settings. For U.S.-flagged vessels and facilities, the U.S. Coast Guard Maritime Cybersecurity Assessment and Annex Guide (MCAAG) lays out a step-by-step approach for identifying cyber-enabled systems, pinpointing vulnerabilities, and developing remediation plans tailored to Facility Security Assessments and Plans.
Industry-specific resources like the "Cyber Security Onboard Ships" guidelines from ICS and BIMCO translate these broader frameworks into actionable shipboard measures. These include creating asset inventories, monitoring communication links, and conducting regular threat assessments. These frameworks collectively set the stage for implementing the technical and procedural safeguards outlined below.
Technical and Procedural Controls
With a solid framework in place, ship operators can focus on deploying layered technical and procedural defenses. Network segmentation is a must – separating operational/bridge systems, corporate networks, crew zones, and passenger areas using VLANs and firewalls ensures better control and containment. Implement multi-factor authentication (MFA) and assign unique credentials for remote access and administrative functions, steering clear of shared or generic accounts.
For endpoint security, use tools like antivirus software, firewalls, and application whitelisting. Data in transit should always be encrypted, using technologies such as VPNs and TLS. Establish centralized logging and monitoring by collecting logs from critical systems like firewalls, servers, and OT devices. If in-house resources are limited, consider outsourcing to a Security Operations Center (SOC) or managed detection service.
Backup strategies are equally important – maintain offline or hardened backups of critical systems and configurations, and test restoration processes regularly. On the procedural side, conduct cyber awareness training tailored to shipboard roles. This should cover key topics like phishing, proper handling of USB drives, and incident reporting.
Document and enforce access control and change management policies for IT and OT systems. These policies should outline how configuration changes are approved, recorded, and, if necessary, rolled back. Finally, integrate cyber scenarios into emergency drills and incident response plans. Examples include handling navigation data loss, ransomware attacks on business systems, or disruptions to satellite communications.
Secure Communication Platforms
Passenger and crew communication networks can be a vulnerable entry point for cyberattacks if not properly secured. These networks should be logically and physically separated from ship OT and critical IT systems. Routing between these zones must be tightly controlled, with no direct trust relationships. Any necessary data exchange should occur through secure, monitored interfaces.
Maritime communication platforms simplify the management of security controls, logging, and policies for passenger, crew, and operational communications. These platforms should offer encrypted voice, messaging, and video services between ship and shore. They should also support central identity management, enforce strong password policies, and implement role-based access control. Additionally, bandwidth and access policies should prioritize operational communications over high-volume passenger traffic to ensure mission-critical systems remain unaffected.
For instance, NT Maritime provides secure onboard communication solutions tailored for cruise lines and government or military operations. Their services include encrypted app-to-app calling, app-to-ship PBX calls, ship PBX-to-app calls, app-to-off-ship calls, and integrated messaging and video over ship Wi-Fi. These features allow users to securely connect using their own devices, ensuring reliable and real-time communication while protecting against cyber threats.
When specialized services like Telehealth are involved, additional privacy and security measures – such as handling protected health information – must be incorporated into the network design. Collaborating with maritime-specific providers ensures that security controls and support procedures align with the unique risks faced by cruise, government, or military vessels. Securing communication platforms is a critical part of a layered defense strategy, safeguarding not just ship operations but also the broader network ecosystem.
Governance, Compliance, and Continuous Improvement
Documenting and Reporting Cyber Risk Assessments
Creating a formal cyber risk register is a must for staying audit-ready. Each entry in this register should include essential details: the asset, associated threats, vulnerabilities, existing controls, planned mitigation efforts, the responsible party, target dates, and the residual risk level.
It’s important to maintain controlled records at both the ship and company levels. For vessels and facilities regulated in the U.S., a cyber annex should be added to your Safety Management System or Facility/Vessel Security Plan. This annex should align with Coast Guard requirements outlined in the Maritime Cybersecurity Assessment and Annex Guide (MCAAG). The annex should cover key areas such as its scope, roles (e.g., Company Security Officer and Ship Security Officer), an overview of assets, risk assessment summaries, preventive measures, incident response protocols, business continuity strategies, training requirements, and links to related checklists. Since IMO Resolution MSC.428(98) mandates that cyber risks be addressed under the ISM Code and verified during audits starting January 1, 2021, this documentation is no longer optional – it’s a regulatory requirement. This thorough documentation also serves as the foundation for fleet-wide evaluations.
Fleet-Wide Implementation and Oversight
Once assessments are documented, fleet-level oversight ensures consistency across all vessels. By standardizing risk criteria, scoring methods, and asset categories, individual ship assessments become comparable, enabling effective fleet-wide management. Consolidate ship registers into a centralized dashboard to identify systemic issues – like outdated navigation software across multiple vessels – and rank ships by residual risk. This approach helps prioritize budget allocation and technical support.
A cyber governance committee – including representatives from legal, insurance, operations, and IT/OT teams – should meet quarterly to review fleet-wide risks, incidents, and compliance. This ensures cyber risks are treated as critical safety and business concerns, not just technical challenges.
To establish a fleet-wide minimum cyber baseline, implement mandatory measures such as hardening, logging, backups, and access controls. Verify compliance through internal audits, third-party assessments, and technical checks like vulnerability scans and configuration reviews. If you’re using specialized maritime IT and communication providers like NT Maritime for secure onboard networks and high-speed connectivity, include their performance and security practices in your risk evaluations. This should cover service-level agreements for incident response and updates to communication platforms.
Periodic Reassessment and Improvement
Regular reassessments are key to keeping up with changing threats and regulations. Maritime guidelines suggest reviewing cyber risk assessments at least once a year or whenever significant changes occur, such as system upgrades, network modifications, regulatory updates, or major cyber incidents. For U.S.-regulated vessels and facilities, updates to Coast Guard guidance, MTSA requirements, or critical Navigation and Vessel Inspection Circulars (NVICs) should also trigger a review of your cyber annex and related procedures.
Track key metrics like unresolved critical vulnerabilities, average time to remediation, crew training completion rates, and the frequency of backup and recovery tests. These metrics should be reviewed by senior management to showcase ongoing improvements. Establish a structured lessons-learned process to capture insights from incidents, near-misses, drills, and external threat reports. Use these insights to update policies, the cyber annex, and training materials.
Technical monitoring is also essential. This includes log collection and review for critical systems, intrusion detection for key networks, regular vulnerability scans, and periodic penetration testing – all tailored to the unique constraints of maritime operations. Together, these efforts ensure that ship IT/OT cyber risk management remains aligned with evolving threats and regulatory demands.
Conclusion
Cyber risk assessment isn’t just a good practice – it’s a necessity for running safe, compliant, and efficient ship operations. With the International Maritime Organization (IMO) requiring cyber risk management under the ISM Code and the U.S. Coast Guard enforcing minimum cybersecurity standards, these assessments have become mandatory. Considering that over 90% of global trade relies on shipping, even a single cyber incident can send shockwaves through international supply chains.
This guide provides a clear, step-by-step approach: define the scope, inventory assets, pinpoint vulnerabilities, assess risks, and create mitigation plans to allocate resources wisely. Whether you choose to adopt frameworks like IMCSO’s Cyber Risk Registry, CRASH, or methodologies from classification societies, the secret to success lies in consistency. Using standardized risk criteria, maintaining well-documented risk registers, and assigning clear ownership ensures your efforts align with a broader cyber resilience strategy.
Particular focus should be placed on communication and network security. Ship-to-shore connectivity, remote access systems, crew Wi-Fi, and passenger services are critical for operations but also present tempting targets for cyberattacks. Solutions like NT Maritime’s encrypted networks, role-based access controls, and integrated communication tools are designed to keep these systems secure while supporting mission-critical operations. These measures not only safeguard against threats but also ensure the smooth functioning of essential maritime activities.
FAQs
What’s the difference between IT and OT systems on ships?
IT systems aboard ships are built to handle tasks like communication, entertainment, and administrative operations for both passengers and crew. Their primary focus is on maintaining connectivity, managing data, and improving the overall user experience.
On the other hand, OT systems are dedicated to the ship’s critical operations, such as navigation, propulsion, safety mechanisms, and cargo management. These systems emphasize real-time control and safety because they directly impact the physical processes and essential functions that keep the ship running smoothly.
The main difference between the two lies in their roles: IT systems manage data and communication needs, while OT systems are tasked with ensuring the ship’s core operations run safely and efficiently.
What steps can ships take to protect against GPS spoofing risks?
Ships can tackle GPS spoofing risks by adopting several protective measures. Using multi-layered authentication helps ensure the integrity of GPS signals, while anti-spoofing algorithms can identify and block questionable activities. To further strengthen security, GPS data should be cross-checked with backup navigation systems such as inertial navigation. Keeping an eye out for unusual signal patterns is also key. Additionally, providing regular training for crew members on recognizing and responding to spoofing attempts plays a crucial role in maintaining safe and secure operations.
What are the key steps to comply with IMO Resolution MSC.428(98) for ship IT systems?
To meet the requirements of IMO Resolution MSC.428(98), start by performing a detailed cyber risk assessment to pinpoint any weak spots in your ship’s IT systems. Use the results to put in place strong cybersecurity measures like firewalls, secure access controls, and encryption protocols.
It’s also crucial to have a well-defined incident response plan in place so your team can handle cyber threats swiftly and efficiently. Keep all systems up to date with regular patches to guard against new vulnerabilities. On top of that, focus on using secure communication protocols for critical IT systems to protect sensitive data and ensure smooth operations.
By following these steps, you’ll strengthen your maritime IT systems’ security and stay aligned with the resolution’s standards for safe operations at sea.